Current cybersecurity challenges
Today, cybersecurity needs are everywhere and attacks are becoming more and more sophisticated. Defense against cybercrime therefore requires constant innovation.
Indeed, many solution editors are not short of creativity and reactivity to adapt and develop efficient protection or monitoring tools to thwart the new attacks that emerge every day.
As a result, tools multiply in some organizations. They are sometimes cascaded, sometimes distributed in distinct network areas, and often perform such specific roles that they become redundant. One might think that this complexity is necessary to provide companies with peace of mind when facing threats, but it is much more complicated than that.
My opinion as a cybersecurity architect
As a senior cybersecurity architect with a focus on SIEM related topics, I have witnessed a lot of these scenarios, some of them well thought through, but most of them mismanaged.
What we need to understand is that implementing security snippets all over the network, email, web browsing, encryption (of files/email), backups, mobile devices, access management, privileges, etc. makes it more complex for operational teams to manage.
Indeed, all these solutions which can have different fields of action (from alerting to blocking) must be centralized in order for the data to be aggregated. These integrations are rather time consuming, because there are very few standards, but it doesn’t stop there. Once all these systems are successfully integrated, we need to build an operational team that will monitor the equipment, but also, analyze all the alerts reported by the SIEM. These are sometimes confirmed, but more often than not, they are “false positives”.
That being said, I do not conclude that the investments that some companies have made have been in vain and that a miracle product will one day solve it all. At a time when every object is connected, it is crucial to be able to monitor all incoming and outgoing flows, at any point of the network, but especially in real time and with the least amount of resources.
Artificial Intelligence, a/the solution
Every company has specific needs in terms of cybersecurity, which makes it complicated for editors to adapt and meet all the possible needs of the market.
As a company specialized in cybersecurity consulting, we have built a matrix to support our customers in the most efficient way possible. We have integrated the most innovative technologies of the moment by forming strong partnerships, based on a real ambition to support our clients in optimizing their protection.
Artificial Intelligence solutions, in addition to answering all the problems mentioned above, can perform behavioral analysis and learn automatically, before attacks can evolve to bypass your security. We could compare Artificial Intelligence solutions to an immune system being tested against all kinds of known and unknown viruses. In a way, integrating AI into your information system would be like giving it the ability to adapt to any situation at any time of the day or night.
Indeed, today, despite all the security measures that can be put in place within one’s information system, two major risks remain:
- The lack of vigilance or carelessness committed by staff
- The possibility of existing flaws on devices or applications that are not under control
Some use cases of Artificial Intelligence in cybersecurity
There is no miracle cybersecurity solution, that’s why I propose that we have a look at how our partner Darktrace operates with specific use cases, rather than exposing very technical characteristics:
Cloud misconfiguration
A financial services company was hosting a number of critical servers on virtual machines in the cloud. Some were intended to be publicly accessible, others were not. During the initial configuration of cloud access, the IT team mistakenly left an important server exposed to the Internet when it was supposed to be isolated behind a firewall.
While the security team was completely unaware of the misconfiguration, the exposed server was eventually discovered and targeted by cybercriminals scanning the Internet via Shodan. Within seconds, Darktrace’s AI detected that the device was receiving an unusual number of incoming connection attempts from a wide range of rare external sources and alerted the security team of the threat.
Internal Threat
A junior DevOps engineer at a multinational organization who worked with AWS and Azure was using containerized systems like Docker and Kubernetes. The engineer accidentally downloaded an update that included a crypto miner, which led to an infection on several production systems.
After the initial infection, the malware began sending signals to a C&C (Command and Control) server, which was immediately detected by Darktrace. Once the external connection was established and the attack mission instructions were given, the crypto-malware infection was able to quickly spread through the organization’s infrastructure at machine speed, infecting 20 servers in less than 5 seconds.
Cryptomining
Blockchain and cryptocurrencies regularly make headlines or are at the front of cyber news blogs. It is important to note that AI is a particularly effective resource in this area.
Indeed we have seen recent cyber AI interventions that have discovered and thwarted hundreds of attacks where devices were infected with crypto-mining malware, including:
- A server responsible for opening and closing a biometric door;
- A spectrometer, a medical IoT device that uses light wavelengths to analyze materials;
- 12 servers hidden under the floors of an Italian bank.
Just last year, Darktrace detected an anomalous crypto-mining activity on an enterprise system. Upon investigation, the organization in question traced the anomalous activity to one of its warehouses, where it found what appeared to be ordinary cardboard boxes sitting on a shelf. Opening these boxes revealed a disguised crypto-currency farm, running on the company’s network feed.

Crypto-currency farm detected by Darktrace’s Artificial Intelligence
RDP (Remote Desktop Protocol) attack
The cybercrime business has exploded in recent years, making things even more challenging for businesses. There are now subscription and rental models readily available on the dark web for a range of illegal activities from Ransomware-as-a-Service to private data auctions. As a result, it is becoming increasingly common for attackers to infect servers and sell the use of these bots online. DDoS for hire services offer access to botnets for as little as $20 per hour. In fact, some of these kits are even legal and advertised as “IP stressers” or “booters,” which can be legitimately used to test the resilience of a website, but are often exploited and used to take down sites and networks.
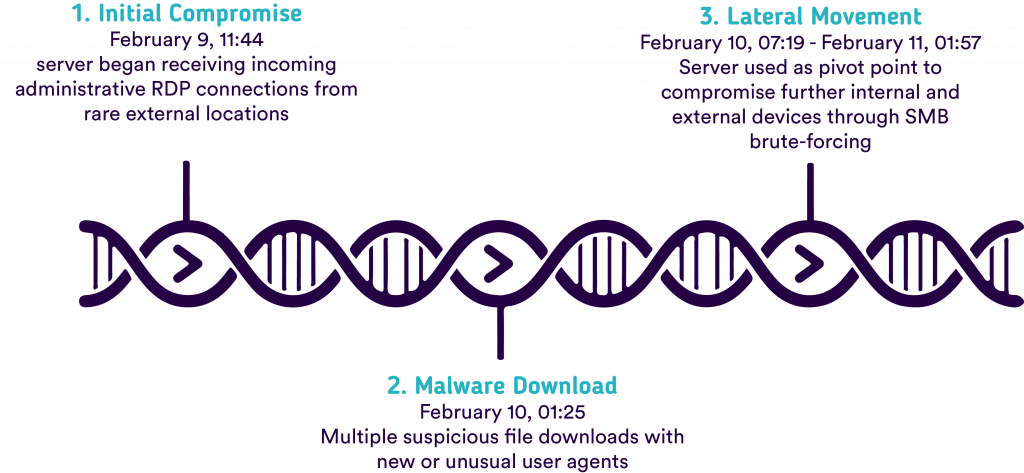
Timeline of an automated Remote Desktop Protocol (RDP) attack
An Internet-accessible Remote Desktop Protocol (RDP) server hosting an online gaming site was recently compromised at a technology company with approximately 500 devices on its network. The attacker used a brute force attack to identify the password and gain remote access to the desktop. That’s when Darktrace’s cyber AI began detecting unusual administrative RDP connections from rare external sites. In this case, the threat actor was likely planning to use the exposed server as a pivot point to infect other internal and external devices, possibly to create a botnet for hire or exfiltrate sensitive information.
The speed of movement and lack of data exfiltration in this incident suggests that the attack was automated, likely using botnet creation tools. The use of automation to accelerate and hide the breach could have had serious consequences had Darktrace not alerted the security team at the earliest stages.
Attacks against Internet-facing RDP servers remain one of the most common initial infection vectors. With the rise of automated scanning services and botnet-like malware, the ease of compromise has increased. It is only a matter of time before exposed servers are exploited. In addition, highly automated attacks are ongoing all the time and can spread rapidly through organizations. In this case, it is vital that security teams are aware of malicious activities on devices as quickly as possible.
Learn more about the applications of Artificial Intelligence in cybersecurity
To learn more about the ways Artificial Intelligence can support your cybersecurity practices and to further explore these real-world use cases with a demonstration of the Darktrace solution, watch our on-demand webinar hosted by Positive Thinking Company’s and Darktrace’s cybersecurity experts.