What is a phishing attack?
Social engineering attacks, such as phishing, are the most common types of cyber-attacks along with ransomware, malware, data breach and Distributed Denial of Service (DDoS).
So common that 91% of cyberattacks start with a phishing email, according to Trend Micro.
But what is phishing exactly?
Phishing is a type of cybersecurity threat that targets users through emails, text messages or sometimes direct messages. The objectives of phishing can be to:
- Steal data (credentials, bank account information, etc.)
- Scare users into paying a ransom
- Gather user’s device information
- Deliver a malicious attachment
Cybercriminals use several tactics to trick users into doing what they want, and these evolve every month. As time goes on, schemes grow more sophisticated and more difficult to detect. They are also increasing in quite a concerning manner. A staggering statistic from the Phishing and Fraud Report (2020) shows that phishing incidents rose 220% during the global pandemic compared to the yearly average.
Phishing is a large concept and getting familiar with the different types of attacks is the first step to protecting yourself and your organization from them.
Email Phishing
Email phishing is the most common type of phishing attack, one that has been around since 1996 (January 2, 1996 to be exact). This attack consists of a generated email that looks legitimate, targeting a huge list of emails. This email is designed to trick the recipient into providing confidential information or browsing a malicious site that an attacker can use to steal data or download a file onto the user’s device.
Example:
- An email coming from someone asking for money;
- An email informing the user that they have been recorded and blackmailing them into transferring money to keep the video from going public.
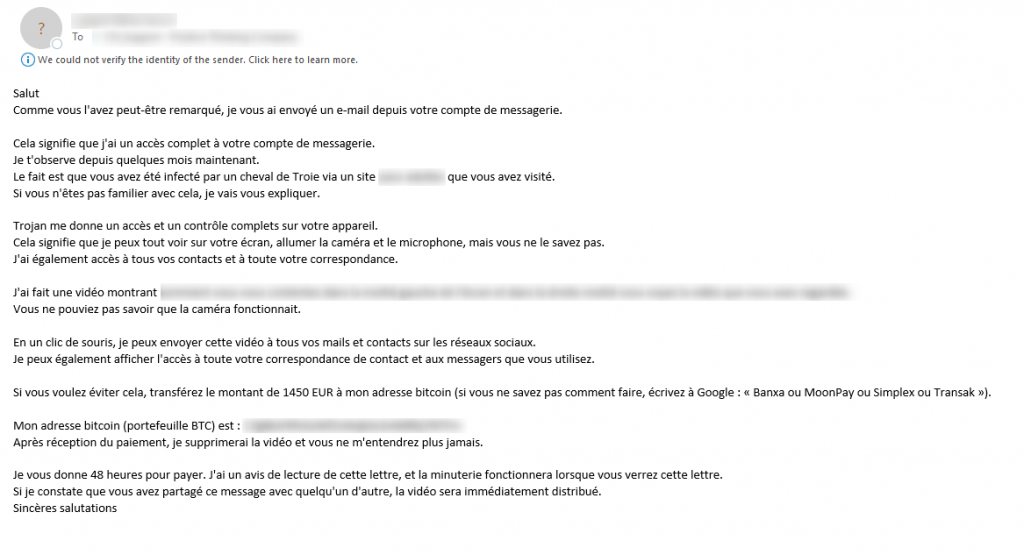
Spear Phishing
Spear phishing is an advanced version of phishing, also the most common one, comprising 65% of all phishing attacks. It is more elaborated and only targets a specific group or type of individuals, such as a company’s HR or financial department employees. With spear phishing, attackers customize their emails with information about the targeted users (first name, last name, phone number, etc.). The targeting company name is often spoofed (disguising a communication from an unknown source as being from a known, trusted source) in order to look more legitimate to the user’s eyes. Most of the time, a spear phishing email will ask targets to access a malicious website where a login form is used to steal credentials. Attackers often play the emergency card for users to respond as quickly as possible.
Example:
- An email coming from a similar domain name, written by someone known, asking you to update your information on the corporate intranet by clicking on the provided link.
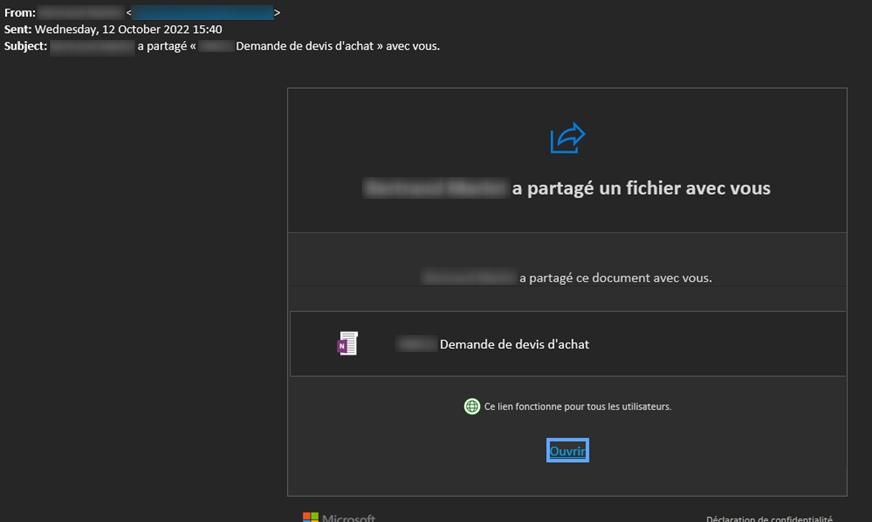
Whaling
In the same category as spear phishing, whaling attacks target only senior executives of a company. These individuals often have deep access to the corporate network. Thus, a successful attack on one of these people can lead to disastrous consequences. (i.e: installation of malware spreading easily due to the access level of the targeted user).
Smishing and Vishing
Smishing and Vishing are both types of phishing that don’t use emails. The first one is done through some form of a text message or SMS (fake UPS delivery message for example). The second one is done through voice phishing, meaning that a criminal will pretend to represent a trusted institution and ask for confidential information.
CEO Fraud
Most of these types of phishing can be combined together to increase attack success. For example, a known attack called “CEO Fraud” could combine Whaling and Vishing. For example, a spoof email is generated coming from the CEO to the secretary asking him/her to make a bank transfer for an important deal. In the next 30 minutes, the attackers call the secretary in order to make the demand more legitimate and more urgent.
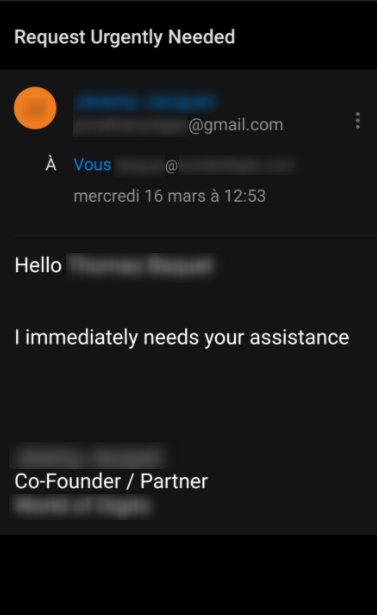
Advanced methods have also been documented recently. To know more about those, Mr. Dox’s blog is a great source of information.
Best practices to protect yourself and your business safe
Here are some of the best practices that will protect you from being phished:
- Look for misspellings in the subject line and content
- Avoid clicking on email links, and go directly to the website when possible
- Stay alert even if the website is in HTTPS! This secure protocol means that nobody between you and the website can read your exchanges, but it doesn’t give any information about the trust of the website
- Always check the mail address, especially the domain name
- Check that the website you use to fill in your credentials uses the HTTPS protocol
- Change your password immediately if you have any doubts
Ready to put your employees at test?
Let our ethical hackers run fictitious phishing campaigns based on scenarios that we establish together to test your employees’ awareness to this type of threat. Contact us here!