A new “Zero day” vulnerability (Follina) has been identified on all versions of Windows.
This vulnerability exists in the Microsoft Support Diagnostic Tool (MSDT). In order for an attacker to exploit it, a special Word or RTF document can be crafted and then sent by mail. Opening it or previewing it in Windows Explorer can trigger code execution with the privileges of the calling application. This vulnerability has been exploited from April 2022.
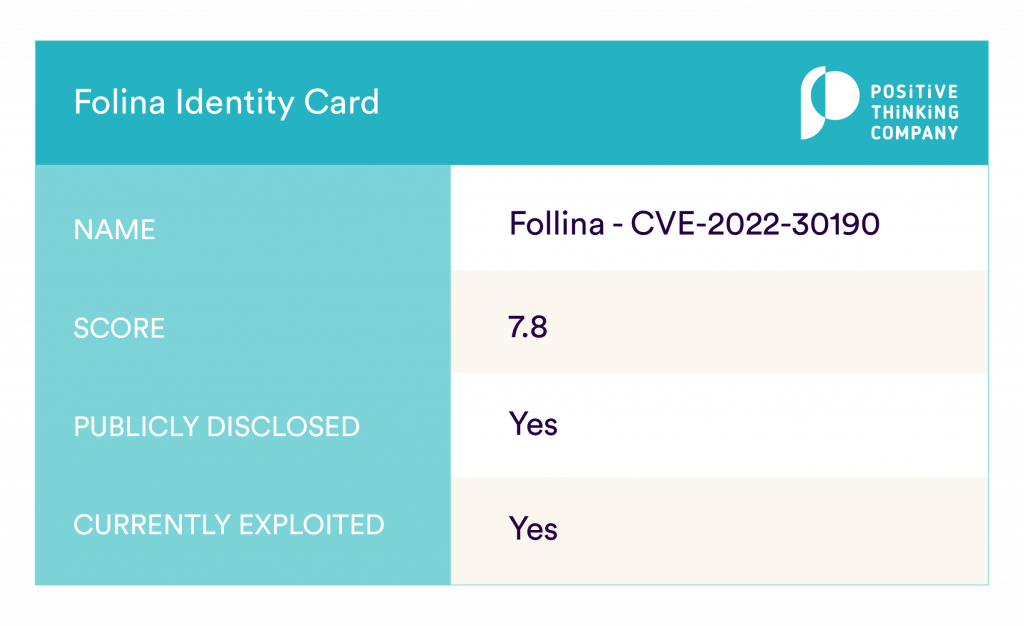
Follina identity card
How to mitigate it?
- Disable the MSDT protocol URL by GPO. This will prevent the utility from being launched as links and thus preventing code execution while Microsoft releases a patch. The utility can still be accessed through Get Help or System Settings.
- Keep your antivirus update. Default payloads available online are already known by some antiviruses.
- Stay updated and follow the vulnerability.
There is another “variant” of this vulnerability. It uses the protocol handler search-ms in order to execute code on the system but requires more user interaction.
Stay alert and contact us for a security overview!
More information
- https://msrc-blog.microsoft.com/2022/05/30/guidance-for-cve-2022-30190-microsoft-support-diagnostic-tool-vulnerability/
- https://www.blackhatethicalhacking.com/news/new-windows-search-zero-day-added-to-microsoft-protocol-nightmare/
- https://www.darkreading.com/threat-intelligence/fighting-follina-application-vulnerabilities-and-detection-possibilities
- https://doublepulsar.com/follina-a-microsoft-office-code-execution-vulnerability-1a47fce5629e