Are you receiving Long Information Security Questionnaires all the time from your potential customers slowing down your sales cycle? Yes, even small businesses and start-ups need compliance. It might be the time to consider ISO 27001 certification?
Contrary to widely held misconceptions, ISO 27001 doesn’t need to hold up your sales cycle (as a matter of fact, it will increase your sales funnel), doesn’t need to cost a fortune or take a year to complete the implementation.
Let us explain why.
There are increasing demands on providing transparency about information security. Every day we read about new vulnerabilities, attacks on businesses and individuals are increasing, and it is becoming more and more complicated to meet legal and regulatory requirements.
This ISO international standard is generally applicable to all organizations, regardless of size, type, or industry. It simply provides the framework for securing your data effectively, instead of specifying exactly what or who needs to be secure. Every business wants to keep its own data and the data of others safe. To be a trusted partner for customers, suppliers and partners, certification to the international ISO 27001 standard is an added value.
The ISO 27001 standard contains the requirements for an information security framework that relies on confidentiality (information is only available to authorized users); integrity (information is accurate and complete) and availability (authorized users have access to information when they need it).
Implementing and certifying your ISO 27001 management system does not mean that your organization can no longer be exposed to cyber crime. However, it does demonstrate that you have performed an information security risk assessment that categorizes the threats and vulnerabilities in your organization and that you have taken all the necessary technical and organizational measures within your capabilities to prevent any incident.
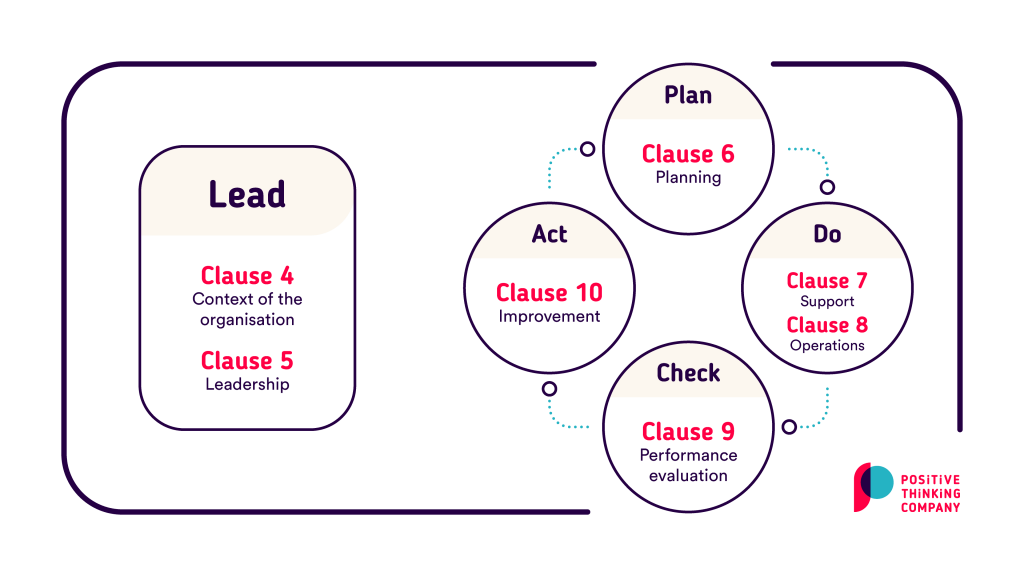
ISO 27001 describes the structure of the framework and uses the Plan-Do-Check-Act cycle (PDCA-cycle). The chapters cover the context of the organization, requirements for management, planning (Statement of Applicability (SoA)), support, operations (including risk assessment, risk mitigation and risk acceptance), evaluation, and continuous improvement.
When you’re looking at implementing the ISO 27001 standard, you’ll need to consider the scope of the controls. Simply, think about which departments of your organization will need to comply with ISO 27001 and implement an ISMS. If you’re a start-up, it is likely that ISO 27001 will apply to your entire organization. This way, you ensure that everyone within the company will contribute to the secure handling of information.
The second part, ANNEX A, deals with concrete measures. It involves a total of 114 so-called controls, divided into 14 chapters.
Overview of the 14 domains of ISO 27001

A5 Information Security Policy (2 controls)
Management needs to provide direction and support for information security in accordance with business requirements and relevant laws and regulations.
In essence, your InfoSec team needs to create an information security policy. This document defines how your organization will set up your ISMS. It should contain a set of policies for management to communicate with employees and external parties (such suppliers, customers).
A6 Organizing information security (7 controls)
Setting up a management framework to initiate, control the and operation of information security within the organization.
Your organization should think about the roles and responsibilities as well as the segregation of duties. Who and how should you communicate with special interest groups and authorities? What about the security during teleworking and the use of mobile devices?
A7 Human resource security (6 controls)
Information security within Human Resources is defined under section A7 of ISO 27001. It is divided into different stages: before, during, and termination or change of employment. All these requirements make sense within HR related processes, including prospective employee screening, communicating the terms and conditions of employment, disciplinary processes, and information and security awareness training.
A8 Asset management (10 controls)
Your company needs to create an inventory of all assets associated with information (including non-digital assets) and assigned ownership. You also should think about the acceptable use, return, labelling, handling, and classification of those assets. Your organization will have to implement controls for media removal and define how to transfer or dispose of media.
A9 Access control (14 controls)
This set of controls handles access control to systems, documents, and software of users. Your organization will need to write an access control policy, manage user access through registration, review and adjust access rights on a regular base. This topic also includes password management, source code restrictions, and the use of secret authentication information.
A10 Cryptography (2 controls)
The cryptographic controls are needed to ensure the protection of the confidentiality, authenticity, and the integrity of the information. Make sure you think about a mature encryption solution for hard disks and review your external information sharing solution(s). Encrypting (personal) information is also an obligation of the GDPR regulation.
A11 Physical and environmental security (15 controls)
The goals of the implementation of these controls is to prevent unauthorised access, damage and interference to information and facilities (buildings, IT rooms, development environment, etc.). It covers secure areas and equipment of the organization. These controls include physical access controls, such as issuing key(s) (badges) or access codes to authorised personnel, and protection against natural disasters, malicious attacks and accidents.
Another set of controls in this section covers how to handle equipment issues such as regularly scheduled maintenance, clean desk and screen policies, delivery of equipment. It also asks for guidelines on how to ensure appropriate protection for unattended equipment.
A12 Operations security (14 controls)
The Operations control of ISO 27001 covers the securing of all operational matters of the processes within the scope of the ISMS. From documentation of procedures and event logging to protection against malware and management of technical vulnerabilities. Change and capacity management also deserve the necessary attention here. Taking and maintaining backups of information and software are also part of these controls.
As an organization, you have a lot of work to do!
A13 Communications security (7 controls)
Within this chapter, a high-level network topology is an added value. Starting from this high-level map, you can dive more in depth to check the settings on firewalls, switches, access point, VLANs. Think also about network architecture and data flow diagrams.
In a clear policy you should define how information can be transferred between parties depending on their information classification. Requirements for confidentiality or non-disclosure agreements reflecting the organization’s needs for the protection of information shall be identified, regularly reviewed and documented.
A14 System acquisition, development, and maintenance (13 controls)
A14 aims to build security into the infrastructure of information systems. This includes requirements for information systems throughout the entire lifecycle, including design, testing, implementation, and analysis. Controls under A14 include securing applications used on public networks (A14.1.2) and protecting application services transactions (A14.1.3).
This is also where the agreements and principles are drawn up about the safe development of software. Most of these checks apply to your developers and system engineers.
A15 Supplier relationships (5 controls)
With these 5 controls on supplier relationships, you must address security within supplier agreements, regularly monitor and assess supplier services, and manage supplier (service) changes to mitigate risk. Here lies the cause of the famous long Information Security Questionnaires you receive.
A16 Information security incident management (7 controls)
A16 is all about management of information security incidents, events and weaknesses. The objective in this Annex A area is to ensure a consistent and effective approach to the lifecycle of incidents, events and weaknesses. First of all, you should have the proper procedures for handling security incidents, including incidents where personal information is involved. (GDPR art 33 & 34) in place. In practice you should be able to demonstrate your reporting on security incidents. When it happened; what was the impact; what was the quick fix you put in place to eliminate the incident? What was the corrective action you implemented after a Root Cause Analysis?
A17 Information security aspects of business continuity management (4 controls)
One of the main reasons for implementing ISO 27001 is to guarantee the availability of the information (systems). A good business continuity plan, inclusive regular tests are key to achieve a level of peace of mind. Redundant equipment where appropriate also always contributes to the availability of information.
A18 Compliance (8 controls)
Follow your own rules! These controls ask your organization to avoid breaches of legal, statutory, regulatory, or contractual obligations related to information security. Basically, it asks that the organization makes sure that it complies with the policies and procedures laid out in the above requirements. A (yearly) penetration testing contributes also to the latest technical compliance.
Pitfalls
ISO 27001 documentation can be the biggest “chunk” of the implementation. Because the management system requires more procedural documents such as policies, the focus on writing those policies takes up a lot of time. But setting up the infrastructure for regularly scheduled reviews, such as access control, also requires time and commitment from all involved within the company.
To avoid writing this documentation (policies, procedures, work instructions) all by yourself, you can work with a consultant who provides templates and guidelines to mature your organization’s awareness quickly.
Bear in mind that an audit is sample-based, but your controls need to continue to operate between annual audits. Otherwise, it’s likely that your organization will risk non-compliance and create more work when the time comes to be audited again. ISMS is a story of continuous improvement!
For small companies (and start-ups), an annual internal audit can be a difficult process. If your company is rather small, it is difficult to get an independent person or team with knowledge of ISO 27001 compliance to carry out the exercise. Often, these organizations will look to external consultants to carry out the internal audit. The internal audit cannot be performed by the same party as your external audit.