The old yet new ransomware kid on the block.
Ransomware is still a booming threat to small and middle-sized enterprises. In essence, a ransomware is a form of advanced malware that will encrypt the drives of a system and ask for “ransom” to get the decryption key and restore functionality to the system. Once the ransom has been paid, you can only hope the attackers supply you with the decryption key to retrieve access to the encrypted systems. Keep in mind that the systems can be reset, and the actual server is not broken, but it is the data on the server that is locked away. The estimated cost of ransomware in 2020 is well over $20 billion dollars, compared to $11.5 billion and $8 billion for 2019 and 2018 respectively.
What is the Ryuk ransomware?
Ryuk is a ransomware that has been around since 2018, but has been evolving ever since in many other variants and flavors. These new variants were recently used in several attacks, notably targeted at the already weakened healthcare industry. Taking advantage of the increasing vulnerability of organisations worldwide due to the COVID-19 pandemic and the surge of remote work, Ryuk attacks have skyrocketed. Through Q3 2019, SonicWall detected just 5,123 Ryuk attacks. Through Q3 2020, they detected 67.3 million Ryuk attacks, accounting for a third of all ransomware attacks this year.
For all variants and “strains” of Ryuk, the main idea is the same and the focus lies on spreading to systems and locking them up.
One of the companies recently hit by Ryuk is a French IT Services Company. While they managed to react fast and efficiently to the threat, their systems still had weeks of significant downtime. In this article we will take a high-level overview into how Ryuk works and how organizations can protect themselves, before, during and after infection.
Before Ryuk is able to lock data away, it needs an entry point into the system. Let us take a closer look on how a typical Ryuk kill chain looks like.
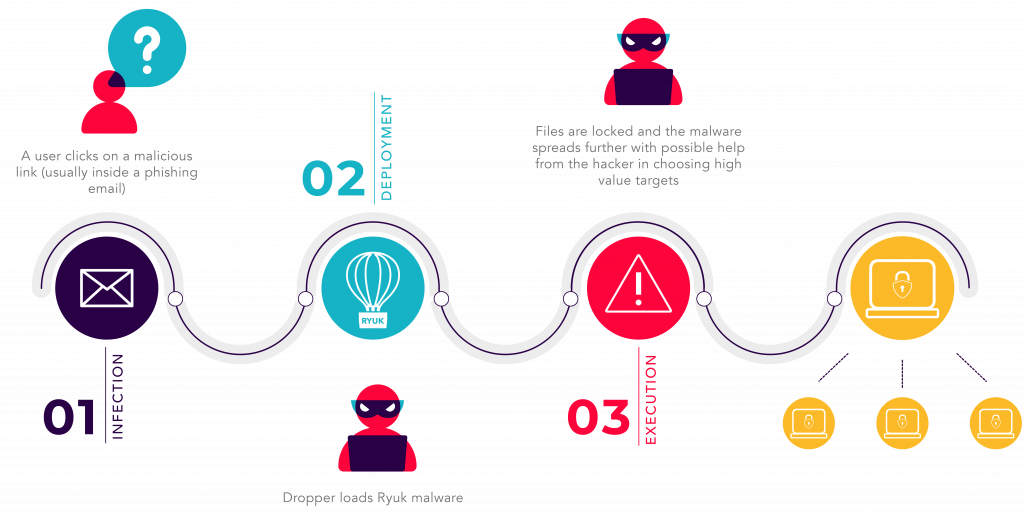
Infection
During this stage, an attacker will gain entry to the company infrastructure in one or multiple ways. Most common and recurring examples of attacks or techniques which can lead to this include:
- Using stolen credentials
- Exploiting outdated and vulnerable softwares
- Phishing with the goal of credential extraction
These techniques are used to install malware onto any workstation or server in the environment. This malware is often called a “dropper” because it enables the attacker to deploy more advanced tools and malware.
Deployment
After the dropper has been installed on the targeted internal system, the next phase of the Ryuk’s attack starts. The dropper will contact the “Command and Control” server to download additional malware that would enable more droppers to be spread on critical devices such as domain controllers and data storages. Usually an attacker will use a compromised server from a third party or an unpatched and vulnerable internal network device to host the actual Ryuk and deploy it to the dropper.
Execution
After Ryuk has been dropped on the target, it will automatically activate after an undetermined period of time. Note that the deployment phase does not end, and the original infection will try to keep spreading droppers throughout the network. Once Ryuk activates, the data will be left encrypted and unrecoverable without the decryption key. This is the part where victims receive lines of text explaining how to buy cryptocurrency and transfer it to the attacker in exchange for the key. Depending on the timeframe when the original infection took place, the entire chain could easily happen overnight. For larger enterprises it will usually happen over the span of several days. Given that there is a higher number of critical targets, bigger organisations will get more time to react and defend themselves, assuming adequate detection and monitoring are in place.
Conclusion and take-aways
All this may sound awfully similar to the big Wannacry ransomware that took a big part of the world by surprise. While the name changed to Ryuk and more advanced code and techniques were used in the recent Ryuk attacks, the underlying problem still makes these attacks very viable and lucrative for malicious actors. It is hard to keep up with the different families and versions of ransomware kits that are being sold to individuals who can barely code, but are still very much able to launch them at smaller organizations. There are a few best practices that can really help make the difference:
- 1. Map, explore and patch all assets in the organization. Do not leave devices, systems or applications unpatched. Penetration tests can help gain insight in where to raise defenses to prevent initial infection in the first place.
- 2. Ensure that critical business data and systems have backups on a hardened or remote location. Remember that malware pulled in by the dropper can find local backups and will prioritize targeting these.
- 3. Create awareness amongst employees to use strong, non-guessable passwords and to be sufficiently suspicious of phishing mails. This can be achieved through security workshops and awareness campaigns. Employees cannot be blamed for falling for phishing or using weak passwords if they were never educated about the dangers of such behaviours. This will drastically improve protection against initial infections.
- 4. Ensure that detection and monitoring are performed across the entire organization to detect, isolate and stop droppers from pulling in additional malware or ransomware. Even in smaller enterprises having a SIEM or similar solutions in place, on site or outsourced, can be of incredible help in stopping the deployment of the more dangerous malware.
- 5. Strong end-point protection to prevent the execution phase is also highly recommended. It can also help prevent the droppers from running in the first place. In many cases, the dropper will pull additional scripts to disable all local protection. Only having an endpoint protection running is not enough but is highly advised as a starting point.
I hope this article has, to some extent, raised awareness about the dangers of ransomwares and how to prevent them from happening. Do not let ransomwares attacks take you by surprise. If you are in doubt of the protections in place in your company, feel free to reach out to us to discuss with our cybersecurity specialists and consult our cybersecurity offering.