For most it went unnoticed, for others, two days ago, one of the most impressive cyber-attack of this decade took place on a mastodon: Twitter.
Not all the details have been revealed yet, but it already presents itself as a textbook case for every company who cares about its brand image.
The scenario
It is becoming clearer, but the hypothesis begins with a twitter support employee who was lured into selling his access codes to the platform’s administration tools via social engineering. He had the privilege, among other things, to modify the authentication methods of users, even the certified ones.
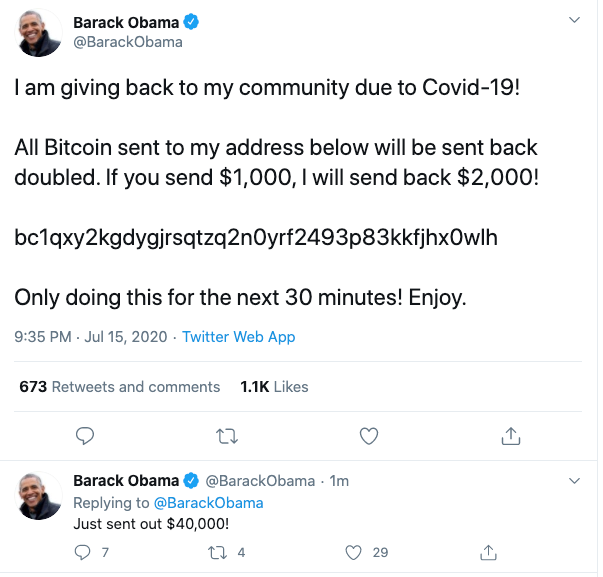
Attackers used this privilege to suppress multi-factor authentication so that public figure accounts were left unprotected. One password change later, the popular accounts of Barack Obama, Elon Musk, Bill Gates and about 130 other high-profile person of influence were sending out a tweet inviting their respective followers to send them virtual money (Bitcoin), because, being generous and under the pretext of a special event, they would return twice as much to them in the process.
The goal of the attackers was to collect the donations of the Internet users without returning them, of course.
The textbook case
ENTRY THROUGH THE BACK DOOR
Finally, regardless of whether the Twitter employee was in cahoots with the attackers or not, a phishing email would have most likely had the same result and thus allowed the attackers to enter the fortress. The point here is that a person who has so many permissions everywhere cannot be left unattended. And even more on certified accounts, which are the value of the company here.
We also note here that, like two thirds of cyber attacks worldwide, this one comes from within. The myth of the hooded man in his disused warehouse is out of date. – Hello #Mr.Robot.
CONDITIONING THROUGH TRUST
Although relatively similar, the tweets sent called on the feelings that followers have with the personality whose identity was stolen. This bias is used in order to put the person in a position of trust and to condition him or her to act in a way they would not normally act.
We have all received spam emails asking for money for the little orphaned and disabled girl on the other side of the world and we are now well aware that these messages are fraudulent. But sometimes it comes directly from a colleague or a friend and the emotions come in. Especially when the attackers are well-informed and “play” with direct information from the person. This is true for a request for money but also to make the target click on a hacker link.
Here the conditioning is amplified by the nature of the accounts selected: they are certified accounts, from influential and therefore trustworthy personalities. While some may be confused by such an a behaviour from an American president like Barack Obama, or a philanthropist like Bill Gates, what about Elon Musk, who is no longer on his first Twitter exploit?
DO IT NOW OR NEVER!
A detail, 5 words at the end of the tweet that could seem trivial: “Only … the next 30 minutes“.
This imperative statement is intended to alarm the reader about the risk of missing an amazing opportunity. Stressed by this eventuality, the person is no longer able to think about the consequences of his or her actions.
This method of conditioning has been used for decades by insurance scams, solar panels, consumer loans and in the digital world also with president scams or phishing of all kinds.
Companies need to raise awareness among their employees and, as can be seen here, their customers, users and partners in order to limit the risks. A Bitcoin transfer should be the first clue to identify an attempted attack, but each individual should also be able to identify the springs present in these tweets.
THE STRIKERS’ VICTORY: THE CLICK
Finally comes the crucial moment. The attack presented here could certainly have done more damage by spreading false information, for example:
- Joe Biden stepping down from the presidential nomination in favor of Barack Obama
- Elon Musk selling his businesses to Amazon, information certified by Jeff Bezos
- Apple announcing the end of iPhones
One can only imagine the financial, political or media impact of such statements corroborated by several certified personalities on a major social network. And, one can only imagine what a competitor could pay for it.
However, the choice of attackers was more modest: make the user click.
Thanks to the above-mentioned strategy , the user is confident, put under pressure by the challenge of missing the opportunity of a short-term gain, he clicks and finds himself on a dedicated page.
This is the crucial moment for any attacker. Amateur attacks will mimic a site with faults, irrelevant images, an endless website name, truncated links, etc. In a major attack like this one, everything is thought to increase the conditioning. The pages (deleted since) have a perfect design, they display real time donations and their return doubled graciously by the generous donor, and even show the remaining time before the opportunity ends.
It’s not hard to imagine the user willingly donating their Bitcoins.
CONCLUSION
The gain of the attack estimated between $100’000 and $400’000 in 3 hours is quite minimal compared to the magnitude of the attack and the means certainly deployed – even if few can boast such an hourly rate.
For Twitter, on the other hand, the result is a fall in the stock market – recovered during the financial year – but above all a damaged image to the point that its CEO had to apologize publicly:

In addition, the unfortunate tweetos who have had their Bitcoin stolen may seek a class action to put the blame on the platform and get their money back, although their personal liability may be involved.
WHICH LESSONS CAN BE LEARNED FROM THIS?
With this cyber attack, we see the biases too often identified in companies.
Too many employees are given privileges out of convenience when these can be an unstoppable means of attack with little effort.
In terms of awareness, risky departments such as finance or management are well off most of the time, but here we see that the risk is transversal. Awareness is an issue for everyone. Both professionally and personally.
The impacts of a potential cyber attack must also be accurately measured: operational costs, legal actions, public opinion, stakeholder relations, etc.
Cyber attacks are the present. For Twitter as for the local SME, it is important to protect the value and integrity of one’s business by identifying and mitigating the risks through concrete actions such as the fine management of privileges, but above all by making individuals aware of cyber crimes.