Penetration testing is an essential aspect of cybersecurity that helps organizations identify vulnerabilities in their networks, systems, and applications. These vulnerabilities, if left unaddressed, could potentially be exploited by malicious actors to gain unauthorized access to sensitive information.
To effectively conduct penetration testing, cybersecurity professionals need access to a variety of tools that can simulate real-world attacks and provide valuable insights into potential vulnerabilities.
In this article, we have compiled a list of the top 10 penetration testing tools that are widely used by cybersecurity professionals. This is a subjective ranking of our pentesters’ favorite tools used during penetration tests, with some good alternatives included.
Whether you are a seasoned professional or just starting out in the field, this article will provide you with valuable information on the most essential penetration testing tools that you should be familiar with. This list will help you to stay updated with the latest trends and techniques in the field and will help you to protect your organization from cyber threats.
Burp proxy
Burp proxy is an interception proxy that enables testers to intercept, modify or replay web communications.
It’s especially useful for web application testing and comes with a variety of useful tools to automate tasks, encode/decode data, scan, and collaborate. It can also be improved with extensions, both from its own library and those developed for specific needs.
| Tool | Description |
|---|---|
| OWASP ZAP | a fully free and open-source interception proxy (unlike Burp) |
| mitmproxy | a Python interception proxy, available as a TUI (Terminal User Interface), a web interface or as a Python library for scripts |
nmap
nmap is a free port scanner used to identify machines on networks and running services hosted on machines. It is used in infrastructure penetration tests as a first step, but it’s also used by network administrators to monitor their networks.
nmap comes with its own script library, which extends the scanner with improved discovery mechanisms, vulnerabilities detection, and more.
nmap is a command line tool, but there is a graphical user interface called zenmap for people not comfortable with terminals.
CrackMapExec
CrackMapExec (or cme) is a Swiss army knife for network penetration testing. This is a set of tools that enables pentesters to attack different services such as LDAP, MSSQL, RDP, SMB, and more.
With this tool, we can enumerate users on services, brute-force passwords, list shares on SMB, and a lot of useful tricks to assess network environments.
Gobuster
Gobuster is a command line tool aimed at brute-forcing URLs on web applications, DNS subdomains, virtual host names or Amazon S3 buckets. It allows us to discover web applications, even those that customers try to hide, such as: https://example.org/admin.

Responder
Responder is a LLMNR, NT-NS and MDNS poisoning tool written in Python, used in Windows networks. It allows attackers to gather information about the machines on a given network, such as user hashes, running OS,and can spawn rogue servers for HTTP, SMB, MSSQL, FTP or LDAP protocols. This script is particularly useful during infrastructure penetration tests.
John The Ripper
Who’s John? We are talking about John the ripper or jtr, a powerful password cracker. Using attacks such as brute force, dictionary, rainbow tables, jtr can recover passwords from different sorts of input, hashed passwords (Linux, Windows, etc.), from encrypted files like PDF, Office files or Zip archives, and much more.
Responder and John together are often a great entry point in an AD network, by gathering hashes and brute-forcing them it can be easy to get valid credentials.
Metasploit
Metasploit is a framework that makes developing, testing and running exploits easier. The exploits are written in Perl and provided by the community, so anyone can contribute. If you find a target with a known vulnerability, chances are good that there is an exploit in the Metasploit database.
Aircrack-ng
Aircrack-ng is a toolkit for WiFi network testing. It helps the pentesters to monitor networks (gather packets), attack networks (replay attack, deauth, fake access point) and even embed the right tool for WEP/WPA cracking.

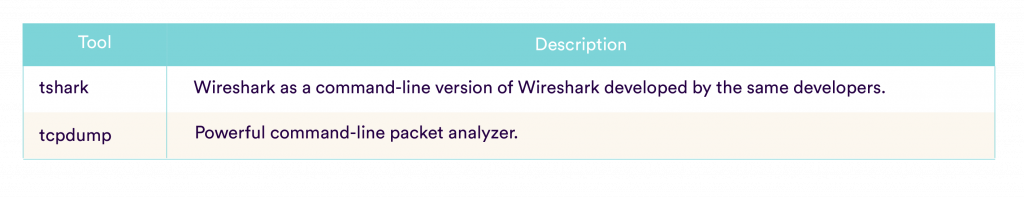
Wireshark
Wireshark is a network traffic and protocol analyzer/sniffer. It aims to gather packets on networks for analysis during penetration testing to discover services that communicate on the network and gather data in packets such as IPs, credentials, encrypted communication for later decryption.
SQLmap
SQLmap is a free and open-source tool specialized in SQL Injection. It automates the detection and exploitation of SQL injection in web application, supports a wide range of database systems, and can enumerate users/tables. With enough knowledge of the database (entry points, credentials), it can even set a direct connection to the database without using the injection anymore.
More on Penetration Testing
- Penetration testing certification: Some tips to ace it
- Performing an API and web application penetration test on a tool connecting intermediaries and taxpayers
- Preventing e-reputation by using OSINT Investigation